Enhance Your Online Safety With Our Revolutionary Internet Security Model: Safeguard Your Digital World Today!
Internet Security Model: A Comprehensive Guide to Protecting Your Online Presence
Introduction
Welcome, readers! In today’s digital age, internet security has become a critical concern for individuals and businesses alike. With cyber threats on the rise, it is essential to understand the various models and measures in place to safeguard your online presence. In this article, we will explore the intricacies of the internet security model and equip you with the knowledge to stay protected in the vast virtual world.
3 Picture Gallery: Enhance Your Online Safety With Our Revolutionary Internet Security Model: Safeguard Your Digital World Today!
Let’s dive in and explore the key aspects of internet security, from its definition to its importance, and from its advantages to its potential drawbacks. By the end of this article, you will have a comprehensive understanding of internet security and be able to take proactive steps towards protecting your digital assets.
The Internet Security Model: Explained

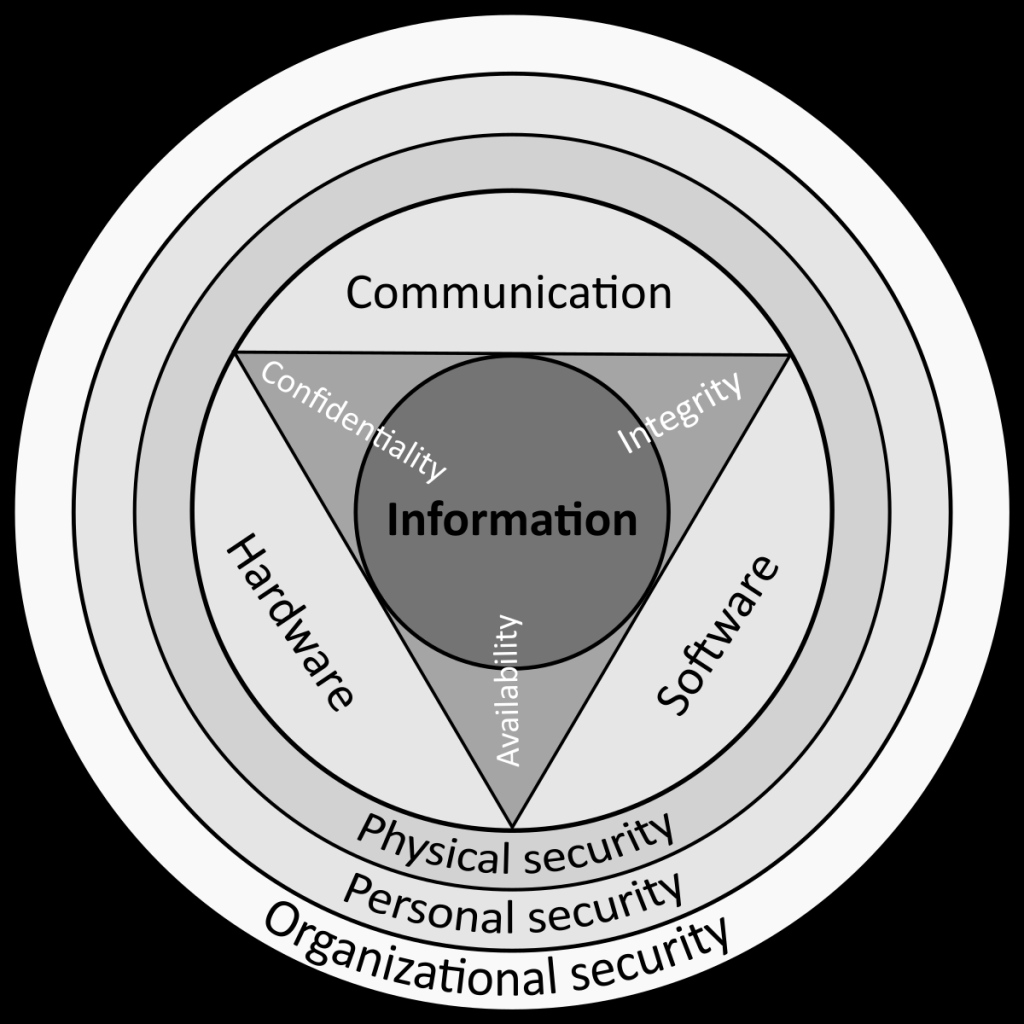
Image Source: wikimedia.org
Before we delve into the details, let’s first establish a clear understanding of what the internet security model entails. Essentially, it refers to the framework and protocols designed to protect computer systems, networks, and data from unauthorized access, cyberattacks, and other potential threats.
In order to achieve robust internet security, multiple layers of protection are implemented, each serving a specific purpose. These layers work together seamlessly to create a comprehensive defense against various types of cyber threats. Let’s take a closer look at each layer and how they contribute to the overall security of your online presence.
1. What is the Internet Security Model?
At its core, the internet security model is a strategic approach to safeguarding computers, networks, and online data from potential threats. It involves a combination of hardware, software, protocols, and human resources working in synergy to protect against unauthorized access, data breaches, malware, and more.

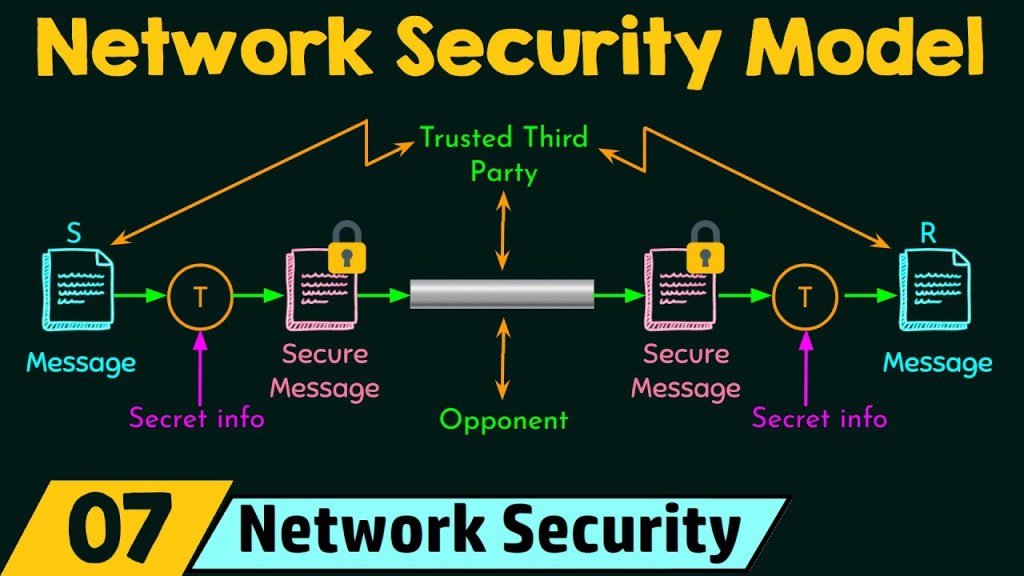
Image Source: ytimg.com
By adopting a multi-layered security framework, businesses and individuals can mitigate the risks associated with cyber threats, ensuring the confidentiality, integrity, and availability of their sensitive information.
2. Who is Responsible for Internet Security?
In the realm of internet security, responsibility is shared among various entities. While individuals are responsible for securing their personal devices and practicing safe online habits, businesses and organizations have a greater role to play in safeguarding their networks, systems, and customer data.

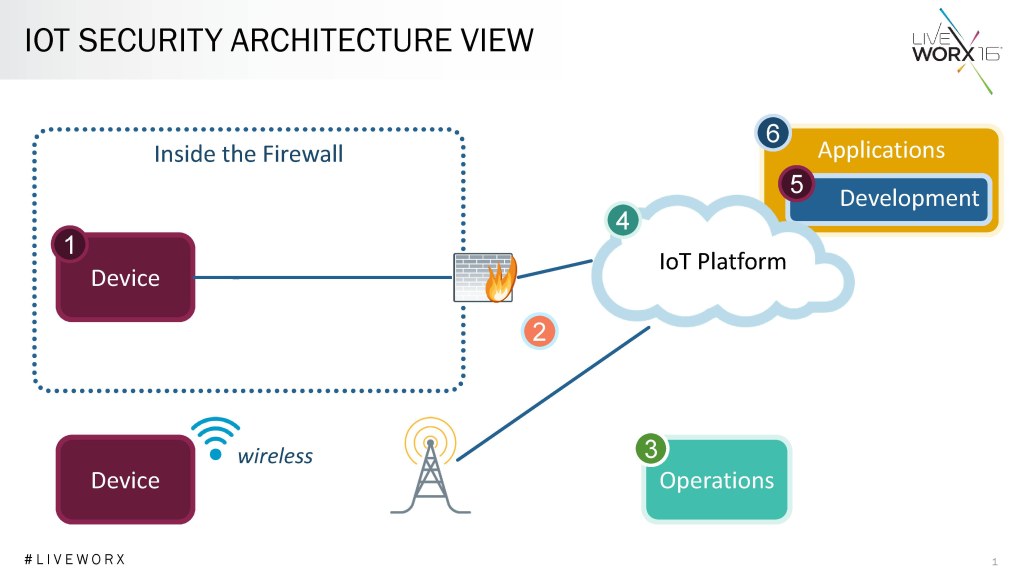
Image Source: iot-now.com
Additionally, government bodies and regulatory authorities establish guidelines and frameworks to ensure compliance with security standards. Internet service providers and technology companies also contribute by implementing security measures within their platforms and services.
3. When Should Internet Security Measures be Implemented?
Internet security measures should be implemented at all times, as cyber threats are persistent and constantly evolving. Whether you are accessing the internet from your home, office, or a public Wi-Fi network, it is crucial to have robust security measures in place.
Moreover, businesses should prioritize the implementation of security protocols during the development and deployment of new systems, ensuring that security is built into the foundation of their digital infrastructure.
4. Where Does Internet Security Apply?
Internet security applies across various domains, including personal devices, home networks, corporate networks, e-commerce platforms, online banking systems, government websites, and more. Essentially, any entity connected to the internet is vulnerable to cyber threats and should have adequate security measures in place.
It is important to acknowledge that even seemingly unimportant devices, such as IoT (Internet of Things) devices, can serve as potential entry points for cybercriminals. Therefore, comprehensive security measures should be implemented across all connected devices and networks.
5. Why is Internet Security Crucial?
The importance of internet security cannot be overstated. Cyber threats not only pose risks to personal privacy but can also have severe consequences for businesses, including financial losses, reputational damage, and legal liabilities.
By investing in robust security measures, individuals and organizations can protect their sensitive data, maintain customer trust, ensure regulatory compliance, and mitigate the potential financial and legal ramifications of cyber incidents.
6. How Does the Internet Security Model Work?
The internet security model operates on the principle of defense in depth, which involves layering multiple security measures to create a holistic defense system. These layers typically include firewalls, antivirus software, intrusion detection and prevention systems, encryption protocols, authentication mechanisms, and employee awareness and training programs.
Each layer serves a specific purpose, such as preventing unauthorized access, detecting and eliminating malware, encrypting data transmissions, and ensuring the integrity of information. By combining these layers, the internet security model provides a comprehensive and robust defense against cyber threats.
Advantages and Disadvantages of the Internet Security Model
Advantages of the Internet Security Model
1. Enhanced Protection: The internet security model offers a multi-layered defense system, providing a higher level of protection against cyber threats.
2. Confidentiality: By encrypting sensitive data and implementing access controls, the internet security model ensures that information remains confidential and only accessible to authorized individuals.
3. Data Integrity: Security measures, such as checksums and digital signatures, guarantee the integrity of data, preventing unauthorized modification or tampering.
4. Regulatory Compliance: Adhering to internet security best practices ensures compliance with industry-specific regulations and data protection laws.
5. Customer Trust: Robust security measures instill confidence in customers, assuring them that their personal information is safe and fostering trust in your organization.
Disadvantages of the Internet Security Model
1. Complexity: Implementing and managing the various layers of the internet security model can be complex and require specialized expertise.
2. Cost: Investing in comprehensive security measures can be costly, especially for small businesses or individuals with limited resources.
3. User Experience: Some security measures, such as multi-factor authentication, may add an extra layer of complexity for users, potentially impacting user experience.
4. False Positives: Security systems, such as intrusion detection systems, may generate false positives, leading to unnecessary alerts or disruptions.
5. Evolving Threats: The ever-evolving nature of cyber threats necessitates continuous updates and adaptations to security measures, which can be time-consuming and resource-intensive.
Frequently Asked Questions (FAQs)
1. What measures can individuals take to enhance their internet security?
Individuals can enhance their internet security by using strong and unique passwords, regularly updating their software and devices, avoiding suspicious links and attachments, and using reputable antivirus software.
2. How can businesses protect themselves from cyber threats?
Businesses can protect themselves from cyber threats by implementing robust firewalls, conducting regular security audits, training employees on security best practices, encrypting sensitive data, and keeping software and systems up to date.
3. Are there any industry-specific internet security standards?
Yes, there are industry-specific internet security standards, such as the Payment Card Industry Data Security Standard (PCI DSS) for the payment card industry and the Health Insurance Portability and Accountability Act (HIPAA) for the healthcare industry.
4. What are some common signs of a potential cyber attack?
Common signs of a potential cyber attack include unusual system behavior, unauthorized access attempts, unexpected data loss, unexplained network traffic, and the presence of unfamiliar files or software.
5. How often should businesses update their internet security measures?
Businesses should update their internet security measures regularly, ideally following a predefined schedule or as soon as security patches and updates are released by vendors.
Conclusion
Friends, we have reached the end of our comprehensive guide to the internet security model. We hope this article has provided you with valuable insights into the various aspects of internet security, from its definition to its advantages and disadvantages.
Remember, safeguarding your online presence requires a proactive and multi-layered approach. By implementing robust security measures, staying informed about the latest threats, and prioritizing user awareness and education, you can significantly reduce the risks posed by cybercriminals.
Now is the time to take action. Evaluate your current security measures, assess any vulnerabilities, and implement the necessary changes to fortify your digital defenses. Stay safe, stay vigilant, and enjoy the benefits of a secure online experience!
Final Remarks
Disclaimer: The information provided in this article is intended for educational purposes only and should not be considered as professional advice. Internet security is a complex and ever-evolving field, and it is recommended to consult with security experts or professionals for personalized guidance tailored to your specific needs.
This post topic: Technology Tutorials


